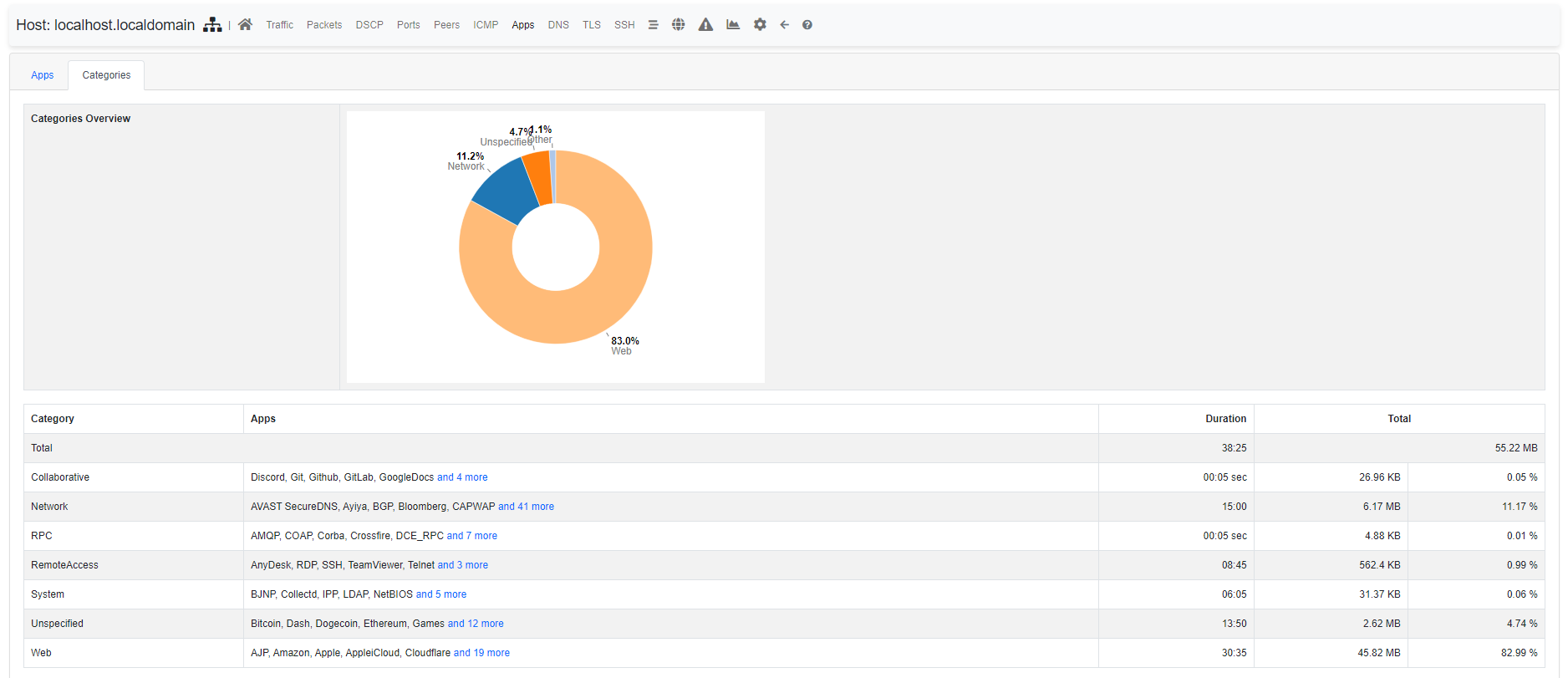
¶ Category
Traditionally DPI was used by blësk NTA to detect flows L7 protocol. With the advent of more and more protocols, speaking about single protocols is often too difficult. Users usually are not interested in the specific protocol but rather in a whole group of protocols. For example, it’s easier to reason about VPN traffic as a whole rather than a particular VPN implementation.
For these reasons, DPI has been extended to provide a logical grouping of protocols, called Categories. With Categories it’s possible, for example, to get an idea of the network traffic of a host.
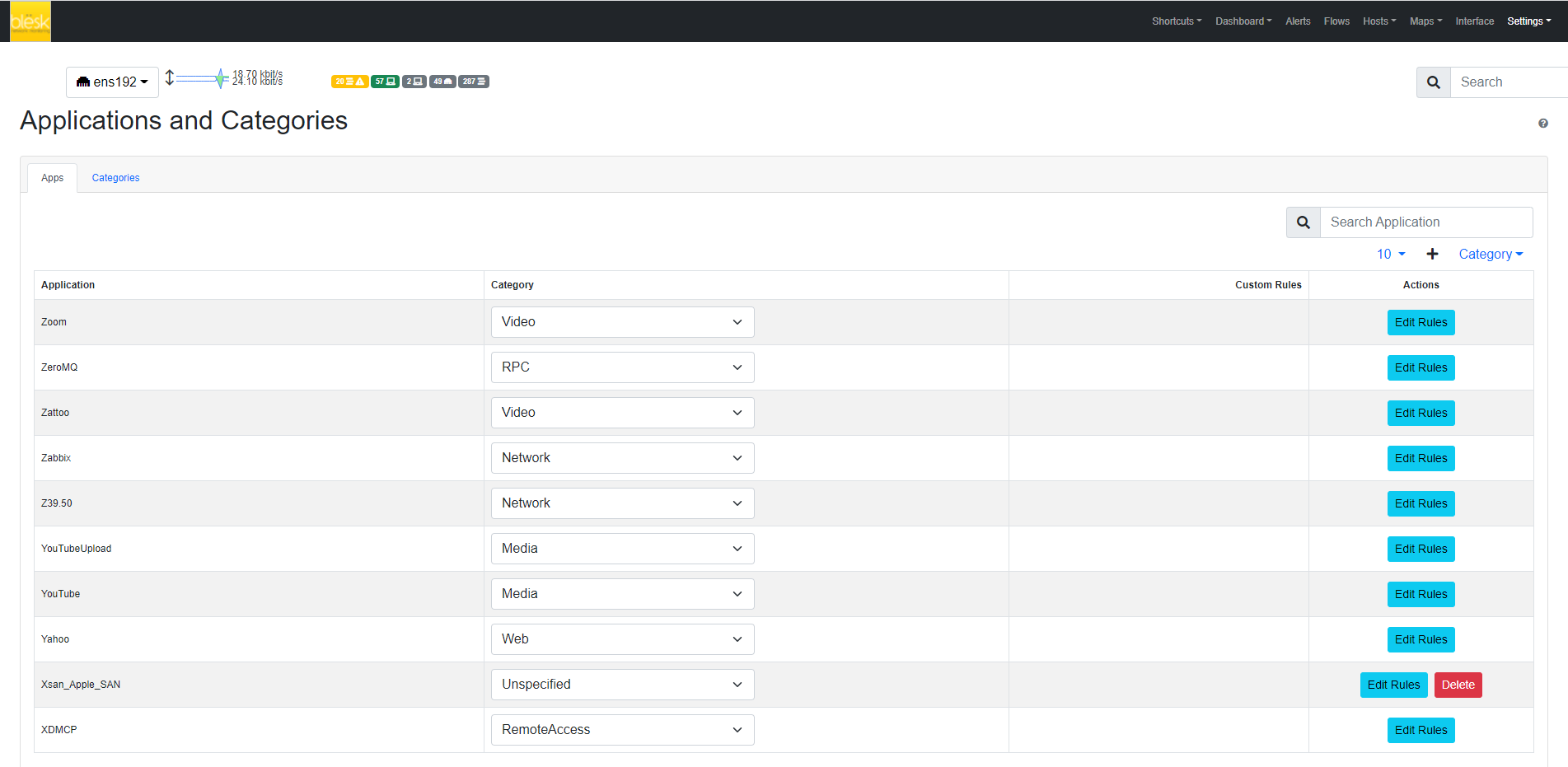
¶ Custom Applications
In the Applications tab, it is possible to configure the category associated with a particular application.
blësk NTA determines the application of a flow via some rules into DPI. However, some additional rules can be specified by the user via the –ndpi-protocols|-p <file> option. The file has the following format:
# host:"<value>",host:"<value>",.....@<subproto>
host:"googlesyndacation.com"@Google
host:"venere.com"@Venere
An example for this configuration file is available here.
blësk NTA also supports editing such files from the GUI. In order to do so, it’s still necessary to use the above option to point to a protos file located into a directory where NTA has the permission to read and write. In practice, in order to enable this feature, NTA should be started with the –ndpi-protocols=/var/lib/ntopng/protos.txt option. If you already have a protos file, move it to /var/lib/ntopng/protos.txt and run
sudo chown ntopng:ntopng /var/lib/ntopng/protos.txt
to prepare it to be used by blësk NTA.
After this feature is enabled, by clicking on the “Edit Rules” button it will be possible to edit application rules directly from the GUI and add new protocols. It’s important to note that rules and new protocols will only be created and applied after a restart of NTA.
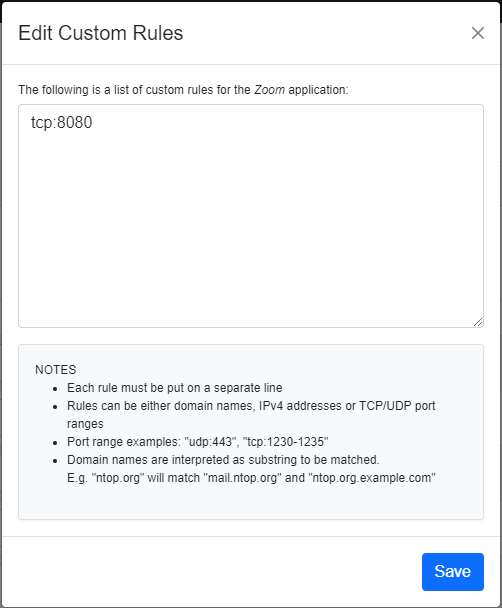
For example, the tcp:8080 rule in the example above tells NTA to treat all the TCP traffic on port 8080 as HTTP. In order to delete a user defined protocol, it is necessary to clear all of its rules and save the changes. The protocol will be deleted after a restart of NTA.
¶ Custom Categories
blësk NTA assigns a default category to the known L7 protocols. Nevertheless, it’s also possible for the user to specify a list of additional hosts to be included into a particular category. NTA provides 5 empty “custom categories” dedicated to this task, but users are also free to modify the other categories.
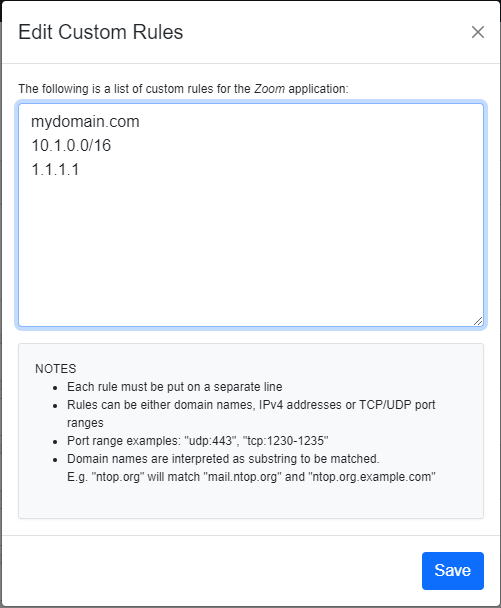
The custom category hosts can be specified via some host-based rules. The host-based rules will be used to perform substring matching on some of the flow information:
- Client/Server IP
- DNS query
- Host SNI
- HTTP Host
If a match is found, the flow category will be set to the corresponding matching category. These rules can be configured from the Categories tab.
Note: host matching based on IP addresses is currently limited to IPv4 flows.
NTA also supports external lists to define custom categories, loaded from text file (local) or online services (e.g. emergingthreats for the Malware category). Since lists are also used to raise alerts (e.g. for hosts in the Malware or Mining category), you may need to add exceptions to those lists, whitelisting selected hosts. This is possible by adding a host to the list, prepending “!” to the IP/hostname (e.g. !1.2.3.4).